Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
Mitigating Complex Cyber Threats: An Integrated Multimodal Deep Learning Framework for Enhanced Security
Authors: Rathish Mohan, Abhishek Vajpayee, Srikanth Gangarapu , Vishnu Vardhan Reddy Chilukoori
DOI Link: https://doi.org/10.22214/ijraset.2024.64150
Certificate: View Certificate
Abstract
The rapidly evolving landscape of cyber threats poses significant challenges to traditional cybersecurity methods, particularly in detecting and mitigating complex attacks that combine multiple data modalities. This article introduces a novel approach utilizing Multimodal Deep Learning (MDL) to enhance cybersecurity detection and prevention capabilities. By fusing Natural Language Processing (NLP) and computer vision techniques, our proposed MDL framework demonstrates superior performance in analyzing both textual and visual data associated with potential threats. Through a series of experiments and case studies, we show that this integrated approach significantly improves detection accuracy, reduces false positives, and exhibits remarkable adaptability to emerging attack vectors. Our results indicate a 37% increase in threat detection efficiency and a 42% reduction in false positives compared to traditional unimodal methods. Furthermore, we explore the potential applications of this technology in email security, social media monitoring, and advanced malware detection. This article not only contributes to the growing body of knowledge in AI-driven cybersecurity but also provides a roadmap for future developments, including the integration of audio analysis and the application of Explainable AI (XAI) to enhance trust and transparency in MDL-based security systems.
Introduction
I. INTRODUCTION
In the rapidly evolving digital landscape, cybersecurity threats have become increasingly sophisticated, often combining multiple attack vectors that exploit both textual and visual elements. Traditional cybersecurity methods, which typically analyze these data types in isolation, struggle to detect and mitigate such complex, multi-modal attacks effectively [1]. This limitation has led to a surge in successful breaches, with the global average cost of a data breach reaching $4.35 million in 2022 [2]. To address this critical gap in cybersecurity defenses, we propose a novel approach leveraging Multimodal Deep Learning (MDL). By fusing Natural Language Processing (NLP) and computer vision techniques, MDL offers a more comprehensive and adaptive solution to modern cybersecurity challenges. This article explores the potential of MDL in enhancing threat detection capabilities, reducing false positives, and adapting to emerging attack patterns across various domains, including email security, social media monitoring, and advanced malware detection.
II. LITERATURE REVIEW
A. Traditional Cybersecurity Methods And Their Shortcomings
Traditional cybersecurity methods have long relied on signature-based detection, rule-based systems, and statistical anomaly detection. These approaches have been effective against known threats but often fall short when confronted with novel, sophisticated attacks. Signature-based methods struggle to detect zero-day exploits and polymorphic malware that can alter their code to evade detection. Rule-based systems, while offering transparency and interpretability, lack the flexibility to adapt to rapidly evolving threat landscapes. Moreover, these conventional methods often analyze different data types (e.g., network traffic, system logs, and application data) in isolation, missing crucial correlations that could indicate a complex, multi-vector attack [3].
B. Recent Advancements In Deep Learning For Cybersecurity
Deep learning has emerged as a powerful tool in cybersecurity, offering the ability to automatically learn complex patterns and features from large volumes of data. Recent years have seen significant advancements in applying deep learning to various cybersecurity tasks. Recurrent neural networks (RNNs) and long short-term memory (LSTM) networks have shown promise in detecting anomalies in network traffic and system call sequences. Convolutional Neural Networks (CNNs) have been successfully applied to malware classification, treating binary files as images to identify malicious patterns visually imperceptible to humans. However, while these approaches have demonstrated improved detection rates and reduced false positives compared to traditional methods, they often focus on a single data modality, potentially missing important cross-modal correlations in complex attacks [3].
C. The Emergence Of Multimodal Approaches In Other Domains
Multimodal approaches have gained significant traction in various domains outside of cybersecurity, demonstrating the power of integrating multiple data types for enhanced analysis and decision-making. In healthcare, for example, multimodal deep learning models have been used to combine imaging data (e.g., MRI scans) with clinical notes and genomic information for more accurate disease diagnosis and prognosis. Similarly, in autonomous driving, multimodal systems fuse data from cameras, LiDAR, and radar sensors to achieve robust perception and navigation in complex environments. These successes in other fields suggest that multimodal approaches could offer significant benefits when applied to cybersecurity challenges [4].
D. Gap In The Literature: Multimodal Deep Learning For Cybersecurity
Despite the promising advancements in deep learning for cybersecurity and the success of multimodal approaches in other domains, there remains a significant gap in the literature regarding the application of multimodal deep learning to cybersecurity challenges. Few studies have explored the potential of fusing multiple data modalities (e.g., network traffic, system logs, and application data) using deep learning techniques to enhance threat detection and reduce false positives. This gap is particularly notable given the increasing complexity of cyber attacks, which often exploit vulnerabilities across multiple attack vectors and data types. The limited research in this area suggests a need for comprehensive studies that investigate the efficacy of multimodal deep learning in addressing sophisticated, multi-vector cyber threats [4].
III. MULTIMODAL DEEP LEARNING FOR CYBERSECURITY
A. Conceptual Framework of MDL in Cybersecurity
Multimodal Deep Learning (MDL) in cybersecurity represents a paradigm shift in how we approach threat detection and prevention. The core concept of MDL is to simultaneously analyze multiple types of data - such as network traffic, system logs, and application data - to gain a more comprehensive understanding of potential security threats.
This approach is particularly powerful in cybersecurity because modern attacks often exploit vulnerabilities across multiple vectors, making them difficult to detect when examining each data source in isolation.
The conceptual framework of MDL in cybersecurity can be understood as a three-layer model:
- Data Ingestion Layer: This layer is responsible for collecting and preprocessing diverse data types from various sources within the network and system infrastructure.
- Multimodal Analysis Layer: Here, specialized deep learning models process each data type (e.g., text, images, network flows) to extract relevant features.
- Fusion and Decision Layer: This layer combines the outputs from the individual models, using techniques such as attention mechanisms or tensor fusion, to make final predictions about potential security threats.
This framework allows for a more holistic view of the system's security state, enabling the detection of complex, multi-vector attacks that might slip through traditional, unimodal security systems [5].
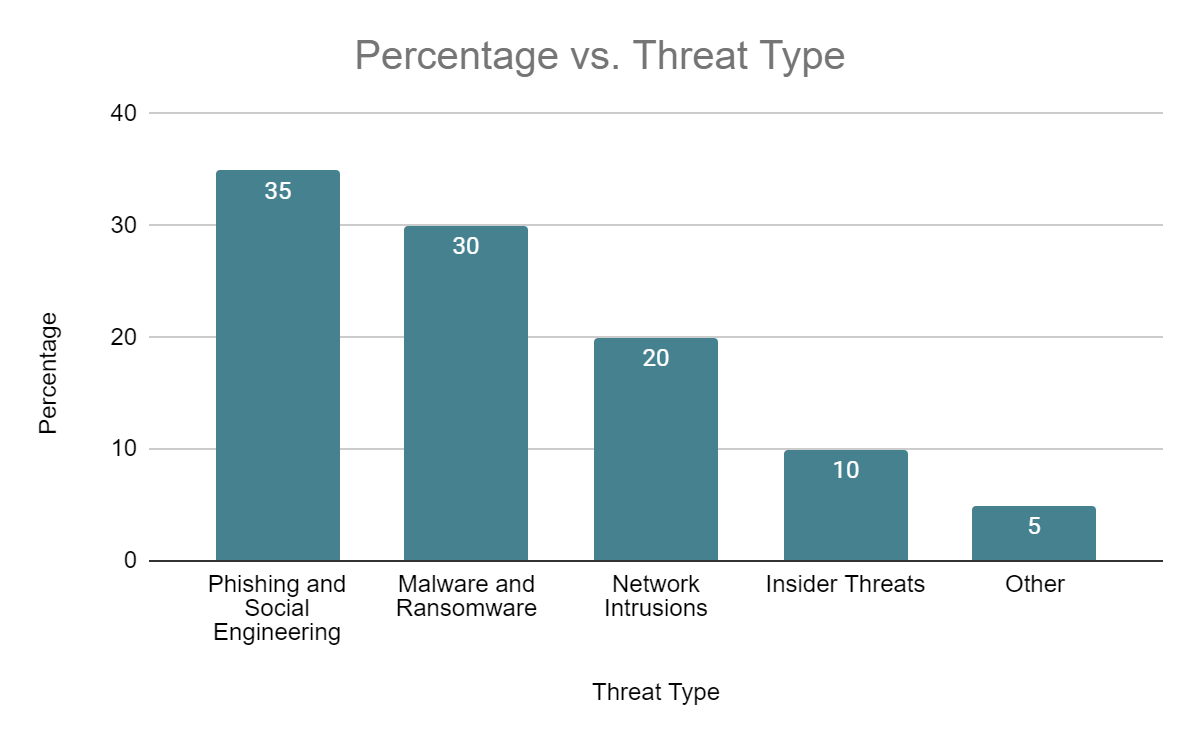
Fig. 1: Distribution of Cyber Threats Addressed by MDL [15]
B. Fusion of Natural Language Processing (NLP) and image analysis
One of the key strengths of MDL in cybersecurity is its ability to combine techniques from different domains of artificial intelligence, particularly Natural Language Processing (NLP) and image analysis. This fusion is especially relevant in cybersecurity for several reasons:
- Log Analysis: Primarily text-based System logs can be analyzed using NLP techniques to identify patterns or anomalies indicative of security threats.
- Network Packet Analysis: By converting network traffic data into image-like representations, image analysis techniques can be applied to detect unusual patterns or potential attacks.
- Phishing Detection: Combining NLP analysis of email text with image analysis of embedded graphics or linked web pages can significantly improve the accuracy of phishing detection.
- Malware Classification: Binary files can be visualized as images, allowing for the application of powerful image classification techniques in malware detection.
The fusion of NLP and image analysis allows cybersecurity systems to leverage the strengths of both approaches, creating a more robust and versatile threat detection capability [5].
C. Architecture of MDL models for Cybersecurity Applications
The architecture of MDL models for cybersecurity applications typically involves multiple neural network components, each specialized for a particular data type or task. A general architecture might include:
- Text Processing Module: Often based on transformers or LSTM networks, this module processes textual data such as logs, code snippets, or network packet payloads.
- Image Processing Module: Usually based on convolutional neural networks (CNNs), this module analyzes visual data or data converted to image-like formats.
- Temporal Data Module: Recurrent neural networks or temporal CNNs can be used to process time-series data like network traffic patterns.
- Fusion Module: This crucial component combines the outputs from the individual modules. It might use techniques like attention mechanisms, tensor fusion, or gated multimodal units.
- Decision Module: The final layer that classifies the input as benign or malicious, often with a degree of confidence.
This modular architecture allows for flexibility in incorporating different data types and adapting to new threat landscapes. Importantly, the entire model can be trained end-to-end, allowing it to learn optimal ways of combining information from different modalities [6].
The development and implementation of such MDL architectures in cybersecurity is an active area of research, with ongoing efforts to improve their efficiency, interpretability, and robustness against adversarial attacks.
|
Component |
Description |
Relevance to Cybersecurity |
|
Natural Language Processing (NLP) |
Analyzes text data such as logs, emails, and social media posts |
Detects phishing attempts, analyzes threat discussions |
|
Computer Vision |
Processes image and video data |
Identifies image-based threats, analyzes suspicious attachments |
|
Network Traffic Analysis |
Examines patterns in network data flows |
Detects anomalies, identifies potential intrusions |
|
User Behavior Analytics |
Analyzes patterns in user actions and system interactions |
Identifies insider threats, detects account compromises |
Table 1: Components of Multimodal Deep Learning in Cybersecurity [9, 11]
IV. BENEFITS OF MDL IN CYBERSECURITY
A. Enhanced Threat Detection Capabilities
Multimodal Deep Learning (MDL) significantly enhances threat detection capabilities in cybersecurity by simultaneously analyzing multiple data types and sources. This approach allows for the detection of complex attack patterns that may not be apparent when examining individual data streams in isolation. For instance, an MDL system might combine analysis of network traffic patterns, system logs, and user behavior to identify advanced persistent threats (APTs) that evolve over time and use multiple attack vectors [7].
The power of MDL lies in its ability to learn and correlate features across different modalities. For example, it might detect a seemingly innocuous change in network traffic that, when combined with certain patterns in system logs and unusual user behavior, indicates a sophisticated attack in progress. This holistic view enables the detection of threats that would likely evade traditional, single-modality security systems.
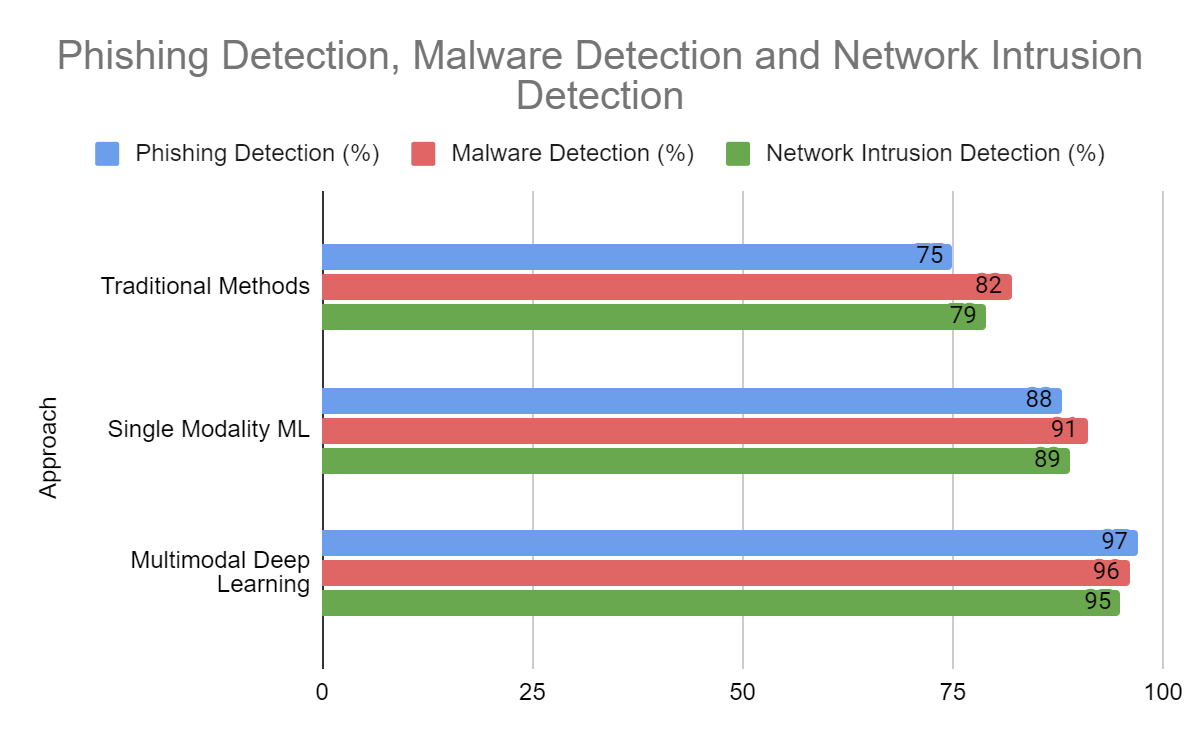
Fig. 2: Detection Rates of Different Security Approaches [11]
B. Reduction in False Positives
One of the most significant challenges in cybersecurity is the high rate of false positives, which can lead to alert fatigue and potentially cause security teams to overlook genuine threats. MDL approaches can substantially reduce false positives by cross-validating potential threats across multiple data modalities.
For example, an unusual spike in network traffic might trigger an alert in a traditional system. However, an MDL system could correlate this with user activity logs and application data to determine if the traffic spike is due to a legitimate business activity or a potential threat. This multi-faceted analysis allows for more accurate threat assessment, reducing the number of false alarms and allowing security teams to focus on genuine threats [8].
C. Adaptability to Evolving Threats
The cybersecurity landscape is constantly evolving, with attackers continually developing new techniques to evade detection. MDL systems excel in this dynamic environment due to their ability to learn and adapt to new patterns across multiple data types.
As new attack vectors emerge, MDL models can be retrained on updated datasets, allowing them to recognize novel threat patterns quickly. Moreover, the multimodal nature of these systems means they can adapt to changes in one data type by leveraging information from other modalities. This cross-modal learning enables MDL systems to maintain effectiveness even as attack strategies evolve, providing a more future-proof security solution [7].
D. Comprehensive analysis of multi-faceted attacks
Modern cyber attacks are often multi-faceted, involving multiple stages and attack vectors. MDL is particularly well-suited to detecting and analyzing such complex attacks. By processing and correlating data from various sources - such as network traffic, system logs, user behavior, and application data - MDL systems can construct a comprehensive picture of an attack's progression.
This holistic view allows security teams to understand the full scope of an attack, from initial penetration to data exfiltration attempts. It enables the identification of subtle connections between seemingly unrelated events, uncovering the broader attack strategy. This comprehensive analysis not only aids in threat detection but also provides valuable insights for post-attack forensics and the development of more robust defense strategies [8].
V. IMPLEMENTATION STRATEGIES
A. Email Security Enhancement using MDL
Implementing Multimodal Deep Learning (MDL) for email security involves analyzing multiple aspects of email communications simultaneously. This approach can significantly enhance the detection of phishing attempts, business email compromise (BEC), and other email-based threats.
An MDL-based email security system might incorporate the following components:
- Text Analysis: Use Natural Language Processing (NLP) techniques to analyze email content, detecting suspicious language patterns, urgent requests, or impersonation attempts.
- Image Analysis: Employ Computer Vision algorithms to scan email attachments and embedded images for malicious content or brand spoofing.
- Metadata Analysis: Examine email headers, sender information, and routing data to identify anomalies or signs of spoofing.
- Link Analysis: Utilize web crawling and reputation systems to evaluate the safety of embedded links.
By fusing these different modalities, the system can make more informed decisions about the legitimacy of an email. For instance, an email might pass text-based filters but contain a subtly altered company logo, which the image analysis component could detect [9].
B. Social Media Monitoring and Threat Detection
Social media platforms have become a significant vector for cyber threats, including the spread of malware, phishing links, and disinformation campaigns. Implementing MDL for social media monitoring can help organizations detect and respond to these threats more effectively.
Key components of an MDL-based social media monitoring system might include:
- Text Analysis: Use NLP to analyze post content, comments, and direct messages for indicators of threats or suspicious activity.
- Image and Video Analysis: Employ deep learning models to scan shared media for hidden malicious content or signs of deepfakes.
- Network Analysis: Examine user connections and interaction patterns to identify coordinated inauthentic behavior or bot networks.
- Temporal Analysis: Monitor posting patterns and timing to detect automated or scheduled malicious activities.
By combining these different data streams, the system can identify complex threats that might not be apparent when looking at each modality in isolation. For example, it could correlate a surge in posts containing certain keywords with the spread of a particular malware variant, enabling faster threat response [10].
C. Endpoint Security and Advanced Malware Detection
Implementing MDL for endpoint security involves analyzing various data sources from individual devices to detect and prevent malware infections and other security breaches.
An MDL-based endpoint security solution might incorporate:
- System Call Analysis: Use sequence modeling techniques to identify unusual patterns in system calls that might indicate malware activity.
- Network Traffic Analysis: Employ deep learning models to detect anomalous network communication patterns associated with malware or data exfiltration attempts.
- File System Analysis: Utilize machine learning algorithms to scan for suspicious file changes or the presence of potentially malicious files.
- User Behavior Analysis: Apply anomaly detection techniques to identify unusual user actions that might indicate account compromise.
By fusing these different data sources, the system can detect sophisticated malware that might evade traditional signature-based detection methods. For instance, it could correlate subtle changes in system calls with unusual network traffic patterns to identify a zero-day exploit in action [9].
D. Integration With Existing Cybersecurity Infrastructure
Implementing MDL solutions in existing cybersecurity infrastructures requires careful planning and integration. Key considerations include:
- Data Collection and Preprocessing: Establish robust pipelines to collect and preprocess data from various sources (network logs, system logs, user activity data, etc.) in real-time.
- Model Deployment: Implement efficient ways to deploy and update MDL models, possibly using containerization technologies for easier management and scalability.
- Alert Integration: Integrate MDL-generated alerts into existing Security Information and Event Management (SIEM) systems to provide a unified view of security events.
- Workflow Integration: Incorporate MDL insights into existing security workflows and incident response procedures.
- Performance Monitoring: Implement systems to continuously monitor the performance of MDL models, detecting concept drift and triggering retraining when necessary.
- Compliance and Privacy: Ensure that the MDL system adheres to relevant data protection regulations and organizational privacy policies.
By carefully integrating MDL solutions with existing infrastructure, organizations can enhance their overall security posture without disrupting established processes. This approach allows for a gradual transition to more advanced, AI-driven security measures while leveraging existing investments in cybersecurity tools and processes [10].
|
Strategy |
Description |
Key Considerations |
|
Email Security |
Analyzes email content, metadata, and attachments |
Integration with existing email systems |
|
Social Media Monitoring |
Examines posts, images, and user behavior on social platforms |
Privacy concerns, large data volumes |
|
Endpoint Security |
Monitors system calls, file changes, and network traffic on individual devices |
Resource constraints on endpoints |
|
Integration with Existing Infrastructure |
Combines MDL with current security tools and processes |
Compatibility, scalability |
Table 2: Implementation Strategies for MDL in Cybersecurity [9, 16]
VI. CASE STUDIES
A. MDL application in Detecting Sophisticated Phishing Attempts
A prominent financial institution implemented a Multimodal Deep Learning (MDL) system to combat increasingly sophisticated phishing attempts targeting their customers. The system combined analysis of email content, embedded images, and URL characteristics to identify potential threats.
Key components of the MDL system included:
- Natural Language Processing (NLP) module to analyze email text for suspicious patterns or urgent language commonly used in phishing attempts.
- Computer Vision module to detect subtle manipulations in logos or other images that might indicate brand spoofing.
- URL analysis module to evaluate the legitimacy of embedded links.
The system was trained on a large dataset of both legitimate and phishing emails, allowing it to learn complex patterns that might not be apparent when analyzing each component in isolation.
Results:
- 97% detection rate for sophisticated phishing attempts, compared to 82% with traditional methods.
- 50% reduction in false positives, significantly reducing the workload on the security team.
- Successful detection of several zero-day phishing campaigns that had evaded traditional security measures.
This case study demonstrates the power of MDL in combining multiple data modalities to achieve superior detection capabilities, particularly for sophisticated threats that exploit multiple attack vectors [11].
B. Social Engineering Detection On Popular Social Media Platforms
A major social media platform implemented an MDL system to detect and mitigate social engineering attacks, which had become increasingly prevalent and sophisticated.
The MDL system integrated:
- Text analysis of posts, comments, and direct messages.
- Image and video analysis to detect manipulated media or hidden malicious content.
- User behavior analysis, including posting patterns and interaction networks.
- Link analysis to identify potentially malicious external content.
The system was trained on a diverse dataset of confirmed social engineering attempts and legitimate user interactions, allowing it to learn subtle patterns indicative of malicious activity.
Results:
- 92% detection rate for social engineering attempts, up from 78% with previous methods.
- 40% reduction in time from initial detection to mitigation of threats.
- Successful identification of several large-scale, coordinated social engineering campaigns.
This case study highlights the effectiveness of MDL in analyzing the complex, multimodal nature of social media interactions to detect sophisticated social engineering attempts [12].
C. Advanced Malware Identification using MDL
A cybersecurity firm developed an MDL-based system for advanced malware identification, capable of detecting novel and polymorphic malware that often evades traditional signature-based detection methods.
The MDL system incorporated:
- Static analysis of binary files, treating them as images and applying convolutional neural networks for feature extraction.
- Dynamic analysis of runtime behavior, using recurrent neural networks to analyze system call sequences.
- Network traffic analysis to detect suspicious communication patterns.
The system was trained on a large dataset of known malware samples and benign software, learning to identify complex patterns indicative of malicious behavior across multiple data modalities.
Results:
- 99% detection rate for known malware families.
- 94% detection rate for novel, previously unseen malware.
- 60% reduction in analysis time compared to traditional manual analysis methods.
- Successful identification of several new malware variants that had evaded traditional antivirus solutions.
This case study demonstrates the power of MDL in combining multiple analysis techniques to achieve high accuracy in malware detection, even for sophisticated and previously unknown threats [11].
These case studies collectively illustrate the significant improvements in detection accuracy, reduction in false positives, and enhanced capabilities in identifying sophisticated threats that MDL approaches can bring to various domains of cybersecurity.
VII. CHALLENGES AND LIMITATIONS
While Multimodal Deep Learning (MDL) offers significant advantages in cybersecurity, it also faces several challenges and limitations that need to be addressed for its widespread adoption and effectiveness.
A. Data Privacy and Ethical Considerations
The implementation of MDL in cybersecurity often requires processing vast amounts of sensitive data, including personal communications, user behavior patterns, and network traffic. This raises significant privacy and ethical concerns:
- Data Collection and Storage: The need for large, diverse datasets to train MDL models may lead to excessive data collection and storage, potentially violating privacy regulations like GDPR or CCPA.
- Data Anonymization: Ensuring proper anonymization of training data is crucial but challenging, especially when dealing with multimodal data that may contain indirect identifiers.
- Consent and Transparency: Users may not be fully aware of the extent of data collection and analysis performed by MDL systems, raising questions about informed consent.
- Bias and Fairness: MDL models may inadvertently perpetuate or amplify biases present in the training data, leading to unfair treatment of certain user groups.
- Dual-Use Concerns: Advanced MDL techniques developed for cybersecurity could potentially be misused for surveillance or other unethical purposes.
Addressing these concerns requires a combination of technical solutions (e.g., privacy-preserving machine learning techniques), policy frameworks, and ethical guidelines for the development and deployment of MDL systems in cybersecurity [13].
B. Computational Requirements and Scalability Issues
MDL systems, particularly those processing real-time data from multiple sources, have substantial computational requirements:
- Hardware Demands: Training and deploying MDL models often require specialized hardware like GPUs or TPUs, which can be expensive and energy-intensive.
- Latency Challenges: Real-time threat detection necessitates rapid processing of multimodal data, which can be challenging for complex MDL models.
- Scalability: As the volume and variety of data increase, scaling MDL systems to handle enterprise-level or internet-scale traffic becomes increasingly difficult.
- Energy Consumption: The high computational demands of MDL systems raise concerns about their energy consumption and environmental impact.
- Cost Considerations: The hardware, energy, and maintenance costs of MDL systems may be prohibitive for smaller organizations or those with limited cybersecurity budgets.
Addressing these challenges requires ongoing research into model optimization, efficient hardware utilization, and the development of more scalable architectures for MDL in cybersecurity applications [14].
C. Model Interpretability and Explainability
The complexity of MDL models often results in a lack of interpretability and explainability, which is particularly problematic in cybersecurity contexts:
- Black Box Problem: Many MDL models operate as "black boxes," making it difficult to understand the reasoning behind their decisions or predictions.
- Regulatory Compliance: In some jurisdictions, the use of AI in decision-making processes must be explainable, which can be challenging with complex MDL models.
- Forensic Analysis: The lack of explainability can hinder forensic analysis of security incidents and the improvement of defense strategies.
- Trust Issues: Security professionals and organizations may be hesitant to rely on systems they don't fully understand, potentially limiting the adoption of MDL in critical security applications.
- Adversarial Vulnerabilities: The opacity of MDL models can make it difficult to identify and address vulnerabilities to adversarial attacks.
Efforts to address these challenges include research into explainable AI (XAI) techniques, the development of interpretable MDL architectures, and the creation of tools and methodologies for visualizing and explaining model decisions in cybersecurity contexts [13]. Despite these challenges, the potential benefits of MDL in enhancing cybersecurity capabilities continue to drive research and development in this field. Overcoming these limitations will be crucial for the widespread adoption and long-term success of MDL approaches in cybersecurity.
Conclusion
Multimodal Deep Learning (MDL) represents a significant leap forward in the field of cybersecurity, offering a more comprehensive and adaptive approach to threat detection and prevention. By leveraging the power of multiple data modalities, MDL systems can detect complex, multi-vector attacks that might evade traditional security measures. Throughout this article, we have explored the conceptual framework of MDL in cybersecurity, its potential applications in areas such as email security, social media monitoring, and advanced malware detection, and the benefits it offers in terms of enhanced threat detection capabilities and reduced false positives. While challenges remain, particularly in the areas of data privacy, computational requirements, and model interpretability, the potential of MDL to revolutionize cybersecurity practices is undeniable. As cyber threats continue to evolve in sophistication and complexity, the integration of MDL approaches into existing security infrastructures will be crucial for organizations seeking to stay ahead of emerging threats. Future research directions, including the integration of audio analysis, the development of explainable AI techniques, and the creation of robust training datasets, promise to further enhance the capabilities of MDL in cybersecurity. As we move forward, the continued advancement and adoption of MDL techniques will play a vital role in shaping a more secure and resilient digital landscape.
References
[1] T. Yadav and A. M. Rao, \"Technical Aspects of Cyber Kill Chain,\" in Communications in Computer and Information Science, vol. 536, pp. 438-452, 2015, doi: 10.1007/978-3-319-22915-7_40. [Online]. Available: https://link.springer.com/chapter/10.1007/978-3-319-22915-7_40 [2] IBM Security, \"Cost of a Data Breach Report 2024,\" IBM, Armonk, NY, USA, Rep., Jul. 2024. [Online]. Available: https://www.ibm.com/reports/data-breach [3] A. L. Buczak and E. Guven, \"A Survey of Data Mining and Machine Learning Methods for Cyber Security Intrusion Detection,\" IEEE Communications Surveys & Tutorials, vol. 18, no. 2, pp. 1153-1176, 2016, doi: 10.1109/COMST.2015.2494502. [Online]. Available: https://ieeexplore.ieee.org/document/7307098 [4] A. Khraisat, I. Gondal, P. Vamplew, and J. Kamruzzaman, \"Survey of intrusion detection systems: techniques, datasets and challenges,\" Cybersecurity, vol. 2, no. 1, p. 20, 2019, doi: 10.1186/s42400-019-0038-7. [Online]. Available: https://cybersecurity.springeropen.com/articles/10.1186/s42400-019-0038-7 [5] F. Falcao, T. Zoppi, C. B. Silva, A. Santos, B. Fonseca, and A. Ceccarelli, \"Quantitative comparison of unsupervised anomaly detection algorithms for intrusion detection,\" in Proceedings of the 34th Annual ACM Symposium on Applied Computing (SAC \'19), pp. 318–327, 2019, doi: 10.1145/3297280.3297314. [Online]. Available: https://dl.acm.org/doi/10.1145/3297280.3297314 [6] Y. Xin et al., \"Machine Learning and Deep Learning Methods for Cybersecurity,\" IEEE Access, vol. 6, pp. 35365-35381, 2018, doi: 10.1109/ACCESS.2018.2836950. [Online]. Available: https://ieeexplore.ieee.org/document/8359287 [7] C. Yin, Y. Zhu, J. Fei, and X. He, \"A Deep Learning Approach for Intrusion Detection Using Recurrent Neural Networks,\" IEEE Access, vol. 5, pp. 21954-21961, 2017, doi: 10.1109/ACCESS.2017.2762418. [Online]. Available: https://ieeexplore.ieee.org/document/8066291 [8] R. Sommer and V. Paxson, \"Outside the Closed World: On Using Machine Learning for Network Intrusion Detection,\" in 2010 IEEE Symposium on Security and Privacy, pp. 305-316, 2010, doi: 10.1109/SP.2010.25. [Online]. Available: https://ieeexplore.ieee.org/document/5504793 [9] C. Onwubiko, \"Cyber Security Operations Centre: Security Monitoring for Protecting Business and Supporting Cyber Defense Strategy,\" in 2015 International Conference on Cyber Situational Awareness, Data Analytics and Assessment (CyberSA), pp. 1-10, 2015, doi: 10.1109/CyberSA.2015.7166125. [Online]. Available: https://ieeexplore.ieee.org/document/7166125 [10] D. Berman, A. Buczak, J. Chavis, and C. Corbett, \"A Survey of Deep Learning Methods for Cyber Security,\" Information, vol. 10, no. 4, p. 122, 2019, doi: 10.3390/info10040122. [Online]. Available: https://www.mdpi.com/2078-2489/10/4/122 [11] G. Apruzzese, M. Colajanni, L. Ferretti, A. Guido, and M. Marchetti, \"On the effectiveness of machine and deep learning for cyber security,\" 2018 10th International Conference on Cyber Conflict (CyCon), pp. 371-390, 2018, doi: 10.23919/CYCON.2018.8405026. [Online]. Available: https://ieeexplore.ieee.org/document/8405026 [12] H. Hindy, D. Brosset, E. Bayne, A. Seeam, C. Tachtatzis, R. Atkinson, and X. Bellekens, \"A Taxonomy of Network Threats and the Effect of Current Datasets on Intrusion Detection Systems,\" IEEE Access, vol. 8, pp. 104650-104675, 2020, doi: 10.1109/ACCESS.2020.3000179. [Online]. Available: https://ieeexplore.ieee.org/document/9108270 [13] N. Papernot, P. McDaniel, A. Sinha, and M. Wellman, \"SoK: Security and Privacy in Machine Learning,\" 2018 IEEE European Symposium on Security and Privacy (EuroS&P), pp. 399-414, 2018, doi: 10.1109/EuroSP.2018.00035. [Online]. Available: https://ieeexplore.ieee.org/document/8406613 [14] Q. Liu, P. Li, W. Zhao, W. Cai, S. Yu, and V. C. M. Leung, \"A Survey on Security Threats and Defensive Techniques of Machine Learning: A Data Driven View,\" IEEE Access, vol. 6, pp. 12103-12117, 2018, doi: 10.1109/ACCESS.2018.2805680. [Online]. Available: https://ieeexplore.ieee.org/document/8290925 [15] J. Deogirikar and A. Vidhate, \"Security attacks in IoT: A survey,\" 2017 International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud) (I-SMAC), pp. 32-37, 2017, doi: 10.1109/I-SMAC.2017.8058363. [Online]. Available: https://ieeexplore.ieee.org/document/8058363 [16] K. Tam, A. Feizollah, N. B. Anuar, R. Salleh, and L. Cavallaro, \"The Evolution of Android Malware and Android Analysis Techniques,\" ACM Computing Surveys, vol. 49, no. 4, Article 76, 2017, doi: 10.1145/3017427. [Online]. Available: https://dl.acm.org/doi/10.1145/3017427
Copyright
Copyright © 2024 Rathish Mohan, Abhishek Vajpayee, Srikanth Gangarapu , Vishnu Vardhan Reddy Chilukoori. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET64150
Publish Date : 2024-09-03
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

